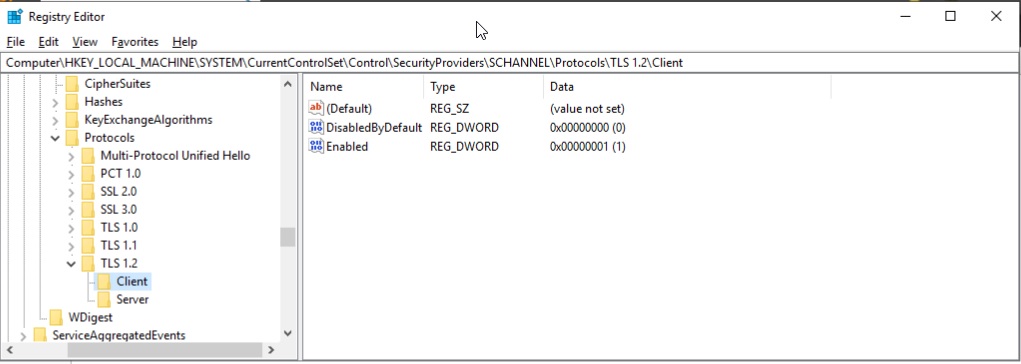
Update the Windows Registry
Start > Run > regedit
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
Open TLS 1.2

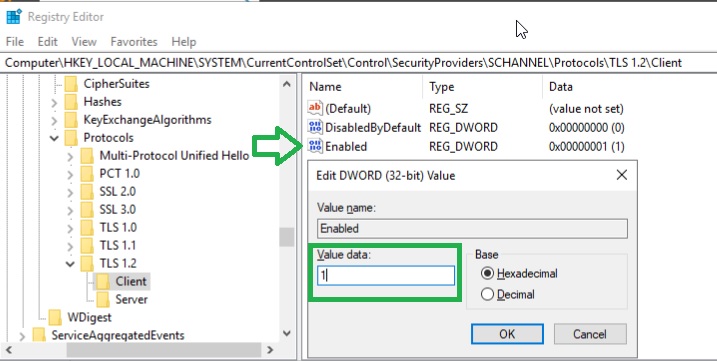
For both Client and Server, double click Enable and set the REG_DWORD to 1. Click Ok, then reboot (but see below first).
Lockdown various protocols for IIS
While you’re configuring TLS, you may as well lock down IIS.
The easiest way to do this is to get Nartac Software’s IIS Crypto. Click here for the download page. If you have used this in the past, always check for new versions as they often have new configurations.
Run the software (there is no installer) > select Templates. For non-PCI related I often use “Best Practices” for internal servers that have no access to the outside world. This is because we may have ancient services running that may still require TLS 1.0.
For production, public servers I would choose PCI 3.x.
Click apply and then reboot.